Sitemap
A list of all the posts and pages found on the site. For you robots out there is an XML version available for digesting as well.
Pages
I am a Senior Lecturer (~Associate Professor) in the Security Systems Research Group of the Lancaster University School of Computing and Communications.
My Open Positions
If you are interested in undertaking a PhD on investigating technical privacy or security challenges in resource-constrained/autonomous cyber physical systems, please contact me by email.
Research
My research has explored a variety of issues involving security, context privacy and trust assessment in resource-constrained systems. This has ranged from context privacy issues in vehicles and wireless sensor networks, and security of different aspects of vehicular systems (including: system analysis, real-world testing and PNT). I am interested in developing and testing practical solutions to security issues based on theoretical foundations.
Bio
I completed my undergraduate Master of Engineering degree in Computer Science at the University of Warwick in 2013 and spent a short period in industry before returning to the Department of Computer Science at the University of Warwick to undertake my PhD supervised by Dr. Arshad Jhumka. I submitted my PhD in May 2018, after which I worked in the Cyber Security Centre in WMG from April 2018 to March 2020. From March 2020 until March 2021 I was a Research Fellow in the Department of Computer Science at the University of Warwick, where I worked on the TEAM project which was funded by PETRAS to perform trust-based task offloading from resource constrained devices to resource rich edge nodes. Since April 2021 I have been a Lecturer at Lancaster University.
Security Lancaster
The Security Systems Group at Lancaster has a number of open PhD and Postdoc positions, please get in contact for further details. The group also runs frequent events and seminars on a wide range of security-focused topics.
Awards and Nominations
- Received the Early Career Researcher of the Year award at the WMG Star Awards 2019
- Received best-in-session presentation award at InfoCom 2017
- Nominated for Warwick Awards for Teaching Excellence for Postgraduates who Teach 2014/15 and 2016/17
Guest Editor
- MDPI Electronics Special Issue on “Cyber Security for Internet of Things”
- MDPI Sensors Special Issue “Dependability of Wireless Sensor Networks”
- MDPI Electronics Special Issue on “Design and Evaluation of Secure Diagnosis and Control Benchmarks and Test-Scenarios for Cyber-Physical Systems”
Programme Committees
- Location Privacy Workshop
- 2023 LPW23 co-located with IEEE Euro S&P
- 2022 LPW22 co-located with IEEE Euro S&P
- 2021 LPW21 co-hosted with ARES
- MDPI Cybersecurity and Privacy Topic Editor [2021]
- IEEE Security and Privacy (IEEE S&P) Shadow PC [2020]
- Formal Methods for Autonomous Systems Workshop (FMAS) [2019]
Reviewed For
- IEEE Security and Privacy (IEEE S&P) Posters
- Security and Communication Networks (SCN)
- ACM Transactions on Cyber-Physical Systems (TCPS)
- IEEE Access
- International Journal of Distributed Sensor Networks (IJDSN)
- Journal of Information Security and Applications (JISA)
- MDPI Sensors and MDPI Electronics
- IEEE Transactions on Industrial Informatics (TII)
- Ad Hoc Networks (ADHOC)
- Computer Communications (COMCOM)
- Vehicular Communications (VEHCOM)
- IEEE Transactions on Software Engineering (TSE)
- Scientific Reports
- IEEE Transactions on Network and Service Management (TNSM)
Student-Staff Liaison Committee (University of Warwick)
Worked with staff and postgraduate students to resolve issues in the PGR Student-Staff Liaison Committee.
- Representative (2016/17, 2017/18)
- Co-Chair (2015/16)
- Secretary (2014/15)
| 2025 | |||
| January 2025 | New paper | ||
| January 2025 | New paper | NewSpace, New Threats — Exploring the Influence of New Entrants to the Space Industry on Cybersecurity. In IEEE AeroConf | |
| 2024 | |||
| September 2024 | Invited Talk | Invited talk on Teaching Penetration Testing | |
| July 2024 | Promotion | Promotion to Senior Lecturer | |
| April 2024 | Funding Awarded | EPSRC Programme Grant: Securing Convergent Ultra-large Scale Infrastructures | |
| February 2024 | Invited Talk | Invited guest lecture at Manchester on Context Privacy | |
| February 2024 | New paper | Enabling Multi-Layer Threat Analysis in Dynamic Cloud Environments. In IEEE Transactions on Cloud Computing | |
| 2023 | |||
| December 2023 | New paper | Security-Minded Verification of Cooperative Awareness Messages. In IEEE Transactions on Dependable and Secure Computing | |
| November 2023 | Invited Talk | Invited talk at the Lancashire Cyber Festival hosted by UCLAN | |
| June 2023 | Outreach | Podcast on privacy threats to cyber physical systems | |
| June 2023 | Funding Awarded | EPSRC New Investigator Award to research Generalised Context Privacy | |
| 2022 | |||
| November 2022 | New paper | Quantifying Source Location Privacy Routing Performance via Divergence and Information Loss. In IEEE Transactions on Information Forensics and Security | |
| November 2022 | New paper | Attributes and Dimensions of Trust in Secure Systems. In Proceedings of the 1st International Workshop on Socio-technical Cybersecurity and Resilience in the Internet of Things | |
| November 2022 | Conference Presentation | Presenting "Threat Modelling Guided Trust-based Task Offloading for Resource-constrained Internet of Things" at the ACM Conference on Embedded Networked Sensor Systems (SenSys 2022) | |
| October 2022 | Article | Article for Lancaster University Management School: "The hackers, the fish tank and the casino: How smart devices could be a hidden flaw in your business's cyber security measures" | |
| September 2022 | Event | First Annual Lancaster Symposium on Systems Security | |
| September 2022 | New paper | Poster: Effectiveness of Moving Target Defense Techniques to Disrupt Attacks in the Cloud. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security | |
| September 2022 | New paper | Poster: Multi-Layer Threat Analysis of the Cloud. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security | |
| August 2022 | New paper | Towards Effective Performance Fuzzing. In The 33rd IEEE International Symposium on Software Reliability Engineering Workshops | |
| August 2022 | New paper | SlowCoach: Mutating Code to Simulate Performance Bugs. In The 33rd IEEE International Symposium on Software Reliability Engineering | |
| June 2022 | Invited Talk | Invited talk at the Academic Centres of Excellence in Cyber Security Research Conference 2022 | |
| May 2022 | New paper | Information Management for Trust Computation on Resource-constrained IoT Devices. In Future Generation Computer Systems | |
| April 2022 | Outreach | Recorded talk on 'Automating Threat Modelling' to SMEs for Lancashire Cyber Foundry | |
| January 2022 | New paper | Threat Modelling Guided Trust-based Task Offloading for Resource-constrained Internet of Things. In ACM Transactions on Sensor Networks | |
| 2021 | |||
| October 2021 | Outreach | Wildlife Conservation: Can AI Make Poachers the Poached? | |
| June 2021 | Outreach | Introduced Cyber Security to students in Kazakhstan | |
| May 2021 | Conference Presentation | Presented paper "Trust Trackers for Computation Offloading in Edge Based IoT Networks" at IEEE INFOCOM | |
| April 2021 | New job | Lecturer at Lancaster University in the Systems and Security Group of School of Computing and Communications | |
| March 2021 | Conference Presentation | Presented paper "Trust Assessment in 32 KiB of RAM: Multi-application Trust-based Task Offloading for Resource-constrained IoT Nodes" at the ACM Symposium of Applied Computing | |
| February 2021 | New Special Issue | MDPI Electronics Special Issue on Design and Evaluation of Secure Diagnosis and Control Benchmarks and Test-Scenarios for Cyber-Physical Systems | |
| 2020 | |||
| December 2020 | New paper | Trust Trackers for Computation Offloading in Edge-Based IoT Networks. In IEEE INFOCOM | |
| December 2020 | New paper | Trust Assessment in 32 KiB of RAM: Multi-application Trust-based Task Offloading for Resource-constrained IoT Nodes. In The 36th ACM/SIGAPP Symposium on Applied Computing | |
| July 2020 | Success Story | Spirent partners with WMG to develop cyber-security services across Connected and Automated Mobility markets | |
| May 2020 | Funding Awarded | PETRAS SRF funding to investigate trust-based task offloading in IoT systems | |
| 2019 | |||
| September 2019 | Success Story | Cyber security of Connected Autonomous Vehicles trialled | |
| June 2019 | Guest Speaker | ORBIT RRI Ethical Hackathon at Royal Holloway | |
Securing Convergent Ultra-large Scale Infrastructures Programme
The SCULI programme will draw on a unique mix of expertise, spanning sociotechnical approaches, theoretical and applied computer science, to transform the way we conceptualise and deliver cyber security in a world with connectivity at unprecedented scale, prevalence of legacy and non-legacy systems, complex technology stacks, complicated supply chains and myriad intersections of humans and technologies.
Generalised Context Privacy
This project will develop techniques to reduce information adversaries can gain from observing cyber physical systems. Using this the capability to develop new context privacy techniques for new systems and scenarios faster will be provided so novel context privacy threats can be rapidly addressed. Theoretical foundations will be used to support practical deployments.
Independent Review of the Office for Nuclear Regulation's Security Assessment Principles
In March 2017 the UK’s Office for Nuclear Regulation (ONR) introduced the Security Assessment Principles for the Civil Nuclear Industry (SyAPs). As these regulatory principles were a significant departure from previous regulatory approaches, the ONR committed to an independent review after 5 years. In this project the independent review was performed and confidential results were provided to ONR.
Evaluating Trustworthiness of Edge-Based Multi-Tenanted IoT Devices
Resource-constrained IoT devices have typically been used to perform sensing and actuation, however, there is increasing interest in those devices performing decision making. However, if these tasks are computationally or memory intensive, then the IoT devices will not have insufficient resources to execute the tasks. One solution is to offload the tasks from resource-constrained IoT devices to resource-rich Edge nodes. For redundancy multiple Edge nodes should be provisioned, but this raises the question of which Edge node should be selected to perform a task. This project investigated building a middleware to perform task offloading based on a measure of behavioural trust with limited resources (e.g., 32 KiB of RAM).
PNT Cyber Resilience: a Lab2Live Observer Based Approach
Vehicular position, navigation, and timing (PNT) systems are of vital importance to current vehicles, future autonomous vehicles and infrastructure depending on time synchronisation. Existing GNSS infrastructure has limited mitigation to prevent a variety of attacks. This project performed a short feasibility study on practical attacks against a vehicle’s PNT system using a PNT attack emulator.
FAIR-SPACE
Access to space is becoming increasingly cheaper, meaning companies and organisations who were previously priced out of the market are now considering space-based deployments. These deployments may also include novel functionality such as debris collection. New entrants will lack the knowledge that well-established space organisations have about how to secure these systems and the new functionality will increase the ways in which these systems will be attacked. This project looked at ways in which these vulnerabilities could be identified and then formally proved to not be present.
IoT Transport and Mobility Demonstrator
With the vehicle-to-vehicle communications being used to facilitated new functionality, there is a need for new security mechanisms to protect this communication. Much work has already been undertaken to develop these mechanisms, but they are rarely tested in real-world environments. This project took existing security and privacy techniques and performed a deployment at three sites in the UK to test their efficacy.
CAPRI
As connected and autonomous vehicles are expected to become commonplace on roads nationwide, new featured are being integrated into vehicles. This includes functionality such as vehicle-to-vehicle communication and machine learning models. It is important that we investigate and address security issues posed by the larger attack surface before a wide deployment. This project designed a reference architecture which facilitated attack surface analysis of connected autonomous vehicles.
Source Location Privacy for Wireless Sensor Networks
Wireless sensor networks are useful for monitoring events over large areas for example, tracking the location of endangered species. However, by deploying this network to obtain data for conservation, it also reveals context information to an adversary about where the animals are. My PhD involved developing routing algorithms to delay an adversary in their attempt to locate the source of messages in such a network.
Publication Map
The bibtex for all my publications is available from here.
2025
- Awais Rashid, Sana Belguith, Matthew Bradbury, Sadie Creese, Ivan Flechais, and Neeraj Suri.
Security-by-designSecuring a compromised system. In Rossfest Symposium. Cambridge, UK, 25 March 2025.
[ bibtex] [ file] [ project] [ more details] - Sara Cannizzaro, Matthew Bradbury, Sam Maesschalck, Gregory Epiphaniou, and Carsten Maple. NewSpace, New Threats – Exploring the Influence of New Entrants to the Space Industry on Cybersecurity. In IEEE Aerospace Conference. Big Sky, Montana, USA, 1–8 March 2025. IEEE.
[ bibtex] [ file] [ project] [ more details]
2024
- Salman Manzoor, Antonios Gouglidis, Matthew Bradbury, and Neeraj Suri. Enabling Multi-Layer Threat Analysis in Dynamic Cloud Environments. IEEE Transactions on Cloud Computing, February 2024. doi:10.1109/TCC.2024.3365736.
[ bibtex] [ file] [ supplemental] [ more details]
2023
- Marie Farrell, Matthew Bradbury, Rafael C. Cardoso, Michael Fisher, Louise A. Dennis, Clare Dixon, Al Tariq Sheik, Hu Yuan, and Carsten Maple. Security-Minded Verification of Cooperative Awareness Messages. IEEE Transactions on Dependable and Secure Computing, pages 18, December 2023. doi:10.1109/TDSC.2023.3345543.
[ bibtex] [ file] [ project] [ more details]
2022
- Salman Manzoor, Antonios Gouglidis, Matthew Bradbury, and Neeraj Suri. Poster: Multi-Layer Threat Analysis of the Cloud. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, CCS’22, 3419–3421. Los Angeles, CA, USA, 7–11 November 2022. ACM. doi:10.1145/3548606.3563515.
[ bibtex] [ file] [ poster] [ more details] - Salman Manzoor, Antonios Gouglidis, Matthew Bradbury, and Neeraj Suri. Poster: Effectiveness of Moving Target Defense Techniques to Disrupt Attacks in the Cloud. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, CCS’22, 3415–3417. Los Angeles, CA, USA, 7–11 November 2022. ACM. doi:10.1145/3548606.3563514.
[ bibtex] [ file] [ poster] [ more details] - Matthew Bradbury, Daniel Prince, Victoria Marcinkiewicz, and Tim Watson. Attributes and Dimensions of Trust in Secure Systems. In Proceedings of the 12th International Conference on the Internet of Things, STaR-IoT’22, 179–186. Delft, Netherlands, 7 November 2022. ACM. doi:10.1145/3567445.3571105.
[ bibtex] [ file] [ presentation] [ more details] - Yiqun Chen, Matthew Bradbury, and Neeraj Suri. Towards Effective Performance Fuzzing. In The 33rd IEEE International Symposium on Software Reliability Engineering Workshops, ISSREW, 128–129. Charlotte, North Carolina, USA, 31 October – 3 November 2022. doi:10.1109/ISSREW55968.2022.00055.
[ bibtex] [ file] [ presentation] [ dataset] [ more details] - Yiqun Chen, Oliver Schwahn, Roberto Natella, Matthew Bradbury, and Neeraj Suri. SlowCoach: Mutating Code to Simulate Performance Bugs. In The 33rd IEEE International Symposium on Software Reliability Engineering, ISSRE, 274–285. Charlotte, North Carolina, USA, 31 October – 3 November 2022. doi:10.1109/ISSRE55969.2022.00035.
[ bibtex] [ file] [ presentation] [ dataset] [ more details] - Matthew Bradbury and Arshad Jhumka. Quantifying Source Location Privacy Routing Performance via Divergence and Information Loss. IEEE Transactions on Information Forensics and Security, 17:3890–3905, 2022. doi:10.1109/TIFS.2022.3217385.
[ bibtex] [ file] [ project] [ more details] - Matthew Bradbury, Arshad Jhumka, and Tim Watson. Information Management for Trust Computation on Resource-constrained IoT Devices. Future Generation Computer Systems, 135:348–363, 2022. doi:10.1016/j.future.2022.05.004.
[ bibtex] [ file] [ dataset] [ project] [ more details] - Matthew Bradbury, Arshad Jhumka, Tim Watson, Denys Flores, Jonathan Burton, and Matthew Butler. Threat-Modeling-Guided Trust-Based Task Offloading for Resource-Constrained Internet of Things. ACM Transactions on Sensor Networks, 18(2):41, 2022. doi:10.1145/3510424.
[ bibtex] [ file] [ presentation] [ dataset] [ project] [ more details]
2021
- Matthew Bradbury, Arshad Jhumka, and Tim Watson. Trust Trackers for Computation Offloading in Edge-Based IoT Networks. In IEEE INFOCOM, 1–10. Vancouver, BC, Canada, 10–13 May 2021. IEEE. doi:10.1109/INFOCOM42981.2021.9488844.
[ bibtex] [ file] [ presentation] [ dataset] [ project] [ more details] - Matthew Bradbury, Arshad Jhumka, and Tim Watson. Trust Assessment in 32 KiB of RAM: Multi-application Trust-based Task Offloading for Resource-constrained IoT Nodes. In The 36th ACM/SIGAPP Symposium on Applied Computing, SAC’21, 1–10. Virtual Event, Republic of Korea, 22–26 March 2021. ACM. doi:10.1145/3412841.3441898.
[ bibtex] [ file] [ presentation] [ dataset] [ project] [ more details] - Matthew Bradbury, Arshad Jhumka, and Carsten Maple. A Spatial Source Location Privacy-Aware Duty Cycle for Internet of Things Sensor Networks. ACM Transactions on Internet of Things, 2(1):1–32, February 2021. doi:10.1145/3430379.
[ bibtex] [ file] [ project] [ more details]
2020
- Matthew Bradbury, Phillip Taylor, Ugur Ilker Atmaca, Carsten Maple, and Nathan Griffiths. Privacy Challenges with Protecting Live Vehicular Location Context. IEEE Access, 8:207465–207484, 2020. doi:10.1109/ACCESS.2020.3038533.
[ bibtex] [ file] [ more details] - Carsten Maple, Matthew Bradbury, Hu Yuan, Marie Farrell, Clare Dixon, Michael Fisher, and Uger Ilker Atmaca. Security-Minded Verification of Space Systems. In IEEE Aerospace Conference. Big Sky, Montana, USA, 7–14 March 2020. IEEE. doi:10.1109/AERO47225.2020.9172563.
[ bibtex] [ file] [ project] - Matthew Bradbury, Carsten Maple, Uger Ilker Atmaca, and Sara Cannizzaro. Identifying Attack Surfaces in the Evolving Space Industry Using Reference Architectures. In IEEE Aerospace Conference. Big Sky, Montana, USA, 7–14 March 2020. IEEE. doi:10.1109/AERO47225.2020.9172785.
[ bibtex] [ file] [ project]
2019
- Carsten Maple, Matthew Bradbury, Anh Tuan Le, and Kevin Ghirardello. A Connected and Autonomous Vehicle Reference Architecture for Attack Surface Analysis. Applied Sciences, 9(23):5101, November 2019. doi:10.3390/app9235101.
[ bibtex] [ file] [ project] - Hu Yuan, Matthew Bradbury, Carsten Maple, and Chen Gu. Throughput Aware Authentication Prioritisation for Vehicular Communication Networks. In 90th IEEE Vehicular Technology Conference (VTC2019-Fall), 1–5. Sep. 2019. doi:10.1109/VTCFall.2019.8891375.
[ bibtex] [ file] - Jasmine Grosso, Arshad Jhumka, and Matthew Bradbury. Reliable Many-to-Many Routing in Wireless Sensor Networks Using Ant Colony Optimisation. In 15th European Dependable Computing Conference (EDCC), 111–118. September 2019. doi:10.1109/EDCC.2019.00030.
[ bibtex] [ file] - Marie Farrell, Matthew Bradbury, Michael Fisher, Louise A. Dennis, Clare Dixon, Hu Yuan, and Carsten Maple. Using Threat Analysis Techniques to Guide Formal Verification: A Case Study of Cooperative Awareness Messages. In Peter Csaba Ölveczky and Gwen Salaün, editors, Software Engineering and Formal Methods, 471–490. Cham, 2019. Springer International Publishing. doi:10.1007/978-3-030-30446-1 25.
[ bibtex] [ file] [ project] - Matthew Bradbury, Arshad Jhumka, and Carsten Maple. The Impact of Decreasing Transmit Power Levels on FlockLab To Achieve a Sparse Network. In Proceedings of the 2nd Workshop on Benchmarking Cyber-Physical Systems and Internet of Things, CPS-IoTBench ‘19, 7–12. New York, NY, USA, April 2019. ACM. doi:10.1145/3312480.3313171.
[ bibtex] [ file] [ presentation] [ dataset] [ project] [ more details] - Chen Gu, Matthew Bradbury, and Arshad Jhumka. Phantom walkabouts: A customisable source location privacy aware routing protocol for wireless sensor networks. Concurrency and Computation: Practice and Experience, 31(20):e5304, 2019. doi:10.1002/cpe.5304.
[ bibtex] [ file] [ project]
2018
- Jack Kirton, Matthew Bradbury, and Arshad Jhumka. Towards optimal source location privacy-aware TDMA schedules in wireless sensor networks. Computer Networks, 146:125–137, 2018. doi:10.1016/j.comnet.2018.09.010.
[ bibtex] [ file] [ project] - Chen Gu, Matthew Bradbury, Jack Kirton, and Arshad Jhumka. A Decision Theoretic Framework for Selecting Source Location Privacy Aware Routing Protocols in Wireless Sensor Networks. Future Generation Computer Systems, 87:514–526, 2018. doi:10.1016/j.future.2018.01.046.
[ bibtex] [ file] [ dataset] [ project] - Matthew Bradbury, Arshad Jhumka, and Matthew Leeke. Hybrid Online Protocols for Source Location Privacy in Wireless Sensor Networks. Journal of Parallel and Distributed Computing, 115:67–81, May 2018. doi:10.1016/j.jpdc.2018.01.006.
[ bibtex] [ file] [ project]
2017
- Matthew Bradbury and Arshad Jhumka. A Near-Optimal Source Location Privacy Scheme for Wireless Sensor Networks. In 16th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), 409–416. August 2017. doi:10.1109/Trustcom/BigDataSE/ICESS.2017.265.
[ bibtex] [ file] [ presentation] [ dataset] [ project] [ more details] - Jack Kirton, Matthew Bradbury, and Arshad Jhumka. Source Location Privacy-Aware Data Aggregation Scheduling for Wireless Sensor Networks. In 37th IEEE International Conference on Distributed Computing Systems (ICDCS), 2200–2205. June 2017. doi:10.1109/ICDCS.2017.171.
[ bibtex] [ file] [ project] - Matthew Bradbury and Arshad Jhumka. Understanding Source Location Privacy Protocols in Sensor Networks via Perturbation of Time Series. In IEEE INFOCOM, 1611–1619. May 2017. doi:10.1109/INFOCOM.2017.8057122.
[ bibtex] [ file] [ presentation] [ project] - Arshad Jhumka and Matthew Bradbury. Deconstructing Source Location Privacy-aware Routing Protocols. In Proceedings of the Symposium on Applied Computing, SAC’17, 431–436. ACM, April 2017. doi:10.1145/3019612.3019655.
[ bibtex] [ file] [ presentation] [ project] - Chen Gu, Matthew Bradbury, and Arshad Jhumka. Phantom Walkabouts in Wireless Sensor Networks. In Proceedings of the Symposium on Applied Computing, SAC’17, 609–616. ACM, April 2017. doi:10.1145/3019612.3019732.
[ bibtex] [ file] [ presentation] [ project]
2016
- Joanna F. Laikin, Matthew Bradbury, Chen Gu, and Matthew Leeke. Towards Fake Sources for Source Location Privacy in Wireless Sensor Networks with Multiple Sources. In 15th IEEE International Conference on Communication Systems (ICCS’16), 1–6. December 2016. doi:10.1109/ICCS.2016.7833572.
[ bibtex] [ file] [ project]
2015
- Chen Gu, Matthew Bradbury, Arshad Jhumka, and Matthew Leeke. Assessing the Performance of Phantom Routing on Source Location Privacy in Wireless Sensor Networks. In 21st IEEE Pacific Rim International Symposium on Dependable Computing (PRDC), 99–108. November 2015. doi:10.1109/PRDC.2015.9.
[ bibtex] [ file] [ project] - Arshad Jhumka, Matthew Bradbury, and Matthew Leeke. Fake source-based source location privacy in wireless sensor networks. Concurrency and Computation: Practice and Experience, 27(12):2999–3020, 2015. doi:10.1002/cpe.3242.
[ bibtex] [ file] [ project] - Matthew Bradbury, Matthew Leeke, and Arshad Jhumka. A Dynamic Fake Source Algorithm for Source Location Privacy in Wireless Sensor Networks. In 14th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), 531–538. August 2015. doi:10.1109/Trustcom.2015.416.
[ bibtex] [ file] [ presentation] [ project]
2014
- Arshad Jhumka, Matthew Bradbury, and Sain Saginbekov. Efficient fault-tolerant collision-free data aggregation scheduling for wireless sensor networks. Journal of Parallel and Distributed Computing, 74(1):1789–1801, 2014. doi:10.1016/j.jpdc.2013.09.011.
[ bibtex] [ file]
2013
- Alasdair Thomason, Matthew Leeke, Matthew Bradbury, and Arshad Jhumka. Evaluating the Impact of Broadcast Rates and Collisions on Fake Source Protocols for Source Location Privacy. In 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), 667–674. July 2013. doi:10.1109/TrustCom.2013.81.
[ bibtex] [ file] [ project]
2012
- Arshad Jhumka, Matthew Bradbury, and Matthew Leeke. Towards Understanding Source Location Privacy in Wireless Sensor Networks through Fake Sources. In 11th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), 760–768. June 2012. doi:10.1109/TrustCom.2012.281.
[ bibtex] [ file] [ presentation] [ project]
PhD Thesis
- Matthew Bradbury. Near Optimal Routing Protocols for Source Location Privacy in Wireless Sensor Networks: Modelling, Design and Evaluation. PhD thesis, University of Warwick, Coventry, UK, May 2018. URL: https://wrap.warwick.ac.uk/115772.
[ bibtex] [ file] [ dataset] [ project]
Technical Reports
- Matthew Bradbury, Elijah Adegoke, Erik Kampert, Matthew Higgins, Tim Watson, Paul Jennings, Colin Ford, Guy Buesnel, and Steve Hickling. PNT Cyber Resilience: a Lab2Live Observer Based Approach, Report 2: Specifications for Cyber Testing Facilities. Technical Report 2, University of Warwick, Coventry, UK, April 2020. Version 1.2. URL: https://wrap.warwick.ac.uk/139522/.
[ bibtex] [ file] [ project] [ more details] - Elijah Adegoke, Matthew Bradbury, Erik Kampert, Matthew Higgins, Tim Watson, Paul Jennings, Colin Ford, Guy Buesnel, and Steve Hickling. PNT Cyber Resilience: a Lab2Live Observer Based Approach, Report 1: GNSS Resilience and Identified Vulnerabilities. Technical Report 1, University of Warwick, Coventry, UK, April 2020. Version 1.0. URL: https://wrap.warwick.ac.uk/139519/.
[ bibtex] [ file] [ project] [ more details] - Carsten Maple, Matthew Bradbury, Miles Elsden, Haitham Cruickshank, Hu Yuan, Chen Gu, and Phillip Asuquo. IoT Transport and Mobility Demonstrator: Cyber Security Testing on National Infrastructure. Technical Report, University of Warwick, Coventry, UK, May 2019.
[ bibtex] [ file] [ project]
LaTeX Thesis Template

FlockLab nRF52840 Dongle Configuration for RIOT and Zephyr
The FlockLab nRF52840 dongle needs specific configuration for both the RIOT and Zephyr operating systems. Using these changes to the OSes allows for serial output to be received from these devices. Note that FlockLab is being discontinued after 2023-06-01.
Writing Papers

Citing RFCs using BibTeX
Generating Bibtex Entries for IETF RFCs and Internet-Drafts
Academia Comics
{% for post in site.talks reversed %} {% include archive-single.html %} {% endfor %}
Lancaster University, UK
Module Convenor for:
- 2021 – current SCC.442 Penetration Testing
- 2021 – 2025 SCC.306 Internet Applications Engineering
SCC.442 Penetration Testing
In this module students are given a fast-paced introduction to Penetration Testing. Students are provided a collection of vulnerable virtual machines running modern operating systems (e.g., Debian 12, Windows Server 2022 and Window Server 2016) to learn how to exploit vulnerabilities in a lab environment. Assessment consists of a formative group penetration testing challenge and a summative individual penetration testing challenge on a range of custom vulnerable machines developed for this module.
A wide range of vulnerabilities are incorporated into the lab environment, such as local privilege escalation with CVE-2023-28252, various web vulnerabilities by incorporating DVWA and OWASP Juice Shop, permission misconfigurations, pivoting, memory attacks, and others.
Vulnerable machines are automatically constructed using Packer and based on templates modified from Bento. Test suites have been developed to ensure that the generated virtual machines are suitably vulnerable.
SCC.306 Internet Applications Engineering
In this module students were given insight into current work building internet applications that is performed in industry. This was achieved by guest lectures from organisations such as the BBC, Tesco, AWS, and others.
- Learnt to analyse website performance using Chrome Developer Tools.
- Experience analysing historical data trends using Google Big Query.
- Learnt how to read and apply web standards such as the Web Content Accessibility Guidelines (WCAG) to identify and fix accessibility issues in a broken website.
Other roles
- 2022 – 2025 Year Two Tutor
University of Warwick, UK
Seminar and lab tutor for:
- 2014 – 2018 CS347 Fault-Tolerant Systems
- 2014 – 2018 CS412 Formal Systems Development
- 2014 – 2018 CS118 Programming for Computer Scientists
- 2015 – 2016 CS241 Operating Systems and Computer Networks
- 2014 – 2016 CS132 Computer Organisation and Architecture
This website does not collect and store your data. No cookies are set by this website.
As this website is hosted by GitHub Pages, GitHub may log accesses to the website. Please see their Privacy Policy for more information.
Blog
August 2021 Reading List
A collection of interesting news articles, features, publications, projects and source code that I find interesting.
September 2021 Reading List
A collection of interesting news articles, features, publications, projects and source code that I find interesting.
October 2021 Reading List
A collection of interesting news articles, features, publications, projects and source code that I find interesting.
November 2021 Reading List
A collection of interesting news articles, features, publications, projects and source code that I find interesting.
December 2021 Reading List
A collection of interesting news articles, features, publications, projects and source code that I find interesting.
January 2022 Reading List
A collection of interesting news articles, features, publications, projects and source code that I find interesting.
Challenges Porting to the nRF52840
I have been working with Giovanni (a visiting PhD student) to port code from a previous project from the Zolertia RE-Mote platform to new nRF52840 DK boards. These boards are much more capable than the Zolertia RE-Motes, not just in terms of computational capability, but also in terms of the ability to debug and instrument them. While we expected to encounter some challenges with the port, the most problematic and time consuming issues ended up being entirely unexpected.
February 2022 Reading List
A collection of interesting news articles, features, publications, projects and source code that I find interesting.
Automating the Testing of CVE-2023-28252
In the Lancaster MSc Cyber Security course, I teach our module on penetration testing. For our labs and assessments this involves developing a number of vulnerable virtual machines that students have access to in a restricted environment. To give confidence that the vulnerabilities can be exploited by students in the labs, lots of time has been devoted to develop tests for these vulnerable machines and the automation of these tests. During the testing of a lab machine involving CVE-2023-28252 which will target a Windows 2022 server, there were challenges getting the automated test to pass while manual testing was able to exploit the vulnerability successfully.
Posts
Projects
Source Location Privacy for Wireless Sensor Networks
Wireless sensor networks are useful for monitoring events over large areas for example, tracking the location of endangered species. However, by deploying this network to obtain data for conservation, it also reveals context information to an adversary about where the animals are. My PhD involved developing routing algorithms to delay an adversary in their attempt to locate the source of messages in such a network.
CAPRI
As connected and autonomous vehicles are expected to become commonplace on roads nationwide, new featured are being integrated into vehicles. This includes functionality such as vehicle-to-vehicle communication and machine learning models. It is important that we investigate and address security issues posed by the larger attack surface before a wide deployment. This project designed a reference architecture which facilitated attack surface analysis of connected autonomous vehicles.
IoT Transport and Mobility Demonstrator
With the vehicle-to-vehicle communications being used to facilitated new functionality, there is a need for new security mechanisms to protect this communication. Much work has already been undertaken to develop these mechanisms, but they are rarely tested in real-world environments. This project took existing security and privacy techniques and performed a deployment at three sites in the UK to test their efficacy.
FAIR-SPACE
Access to space is becoming increasingly cheaper, meaning companies and organisations who were previously priced out of the market are now considering space-based deployments. These deployments may also include novel functionality such as debris collection. New entrants will lack the knowledge that well-established space organisations have about how to secure these systems and the new functionality will increase the ways in which these systems will be attacked. This project looked at ways in which these vulnerabilities could be identified and then formally proved to not be present.
PNT Cyber Resilience: a Lab2Live Observer Based Approach
Vehicular position, navigation, and timing (PNT) systems are of vital importance to current vehicles, future autonomous vehicles and infrastructure depending on time synchronisation. Existing GNSS infrastructure has limited mitigation to prevent a variety of attacks. This project performed a short feasibility study on practical attacks against a vehicle’s PNT system using a PNT attack emulator.
Evaluating Trustworthiness of Edge-Based Multi-Tenanted IoT Devices
Resource-constrained IoT devices have typically been used to perform sensing and actuation, however, there is increasing interest in those devices performing decision making. However, if these tasks are computationally or memory intensive, then the IoT devices will not have insufficient resources to execute the tasks. One solution is to offload the tasks from resource-constrained IoT devices to resource-rich Edge nodes. For redundancy multiple Edge nodes should be provisioned, but this raises the question of which Edge node should be selected to perform a task. This project investigated building a middleware to perform task offloading based on a measure of behavioural trust with limited resources (e.g., 32 KiB of RAM).
Independent Review of the Office for Nuclear Regulation's Security Assessment Principles
In March 2017 the UK’s Office for Nuclear Regulation (ONR) introduced the Security Assessment Principles for the Civil Nuclear Industry (SyAPs). As these regulatory principles were a significant departure from previous regulatory approaches, the ONR committed to an independent review after 5 years. In this project the independent review was performed and confidential results were provided to ONR.
Generalised Context Privacy
This project will develop techniques to reduce information adversaries can gain from observing cyber physical systems. Using this the capability to develop new context privacy techniques for new systems and scenarios faster will be provided so novel context privacy threats can be rapidly addressed. Theoretical foundations will be used to support practical deployments.
Securing Convergent Ultra-large Scale Infrastructures Programme
The SCULI programme will draw on a unique mix of expertise, spanning sociotechnical approaches, theoretical and applied computer science, to transform the way we conceptualise and deliver cyber security in a world with connectivity at unprecedented scale, prevalence of legacy and non-legacy systems, complex technology stacks, complicated supply chains and myriad intersections of humans and technologies.
Publications
PNT Cyber Resilience: a Lab2Live Observer Based Approach, Report 1: GNSS Resilience and Identified Vulnerabilities
Global navigation satellite systems (GNSS) such as GPS and Galileo are vital sources of positioning, navigation and timing (PNT) information for vehicles. This information is of critical importance for connected autonomous vehicles (CAVs) due to their dependence on this information for localisation, route planning, and situational awareness. A downside to solely relying on GNSS for PNT is that the signal strength arriving from navigation satellites in space is weak and currently there is no authentication included in the civilian GNSS adopted in the automotive industry. This means that cyber-attacks against the GNSS signal via jamming or spoofing are attractive to adversaries due to the potentially high impact they can achieve. This report reviews the vulnerabilities of GNSS services for CAVs, as well as detection and mitigation techniques, summarises the opinions on PNT cybertesting sourced from a select group of experts, and finishes with a description of the associated lab-based and real-world feasibility study and proposed research methodology.
A Near-Optimal Source Location Privacy Scheme for Wireless Sensor Networks
Source Location Privacy (SLP) is an important problem when monitoring valuable assets with wireless sensors. It is important that sensitive context information, such as the location of an asset, is not revealed to adversaries. This work aimed to investigate optimal strategies to provide SLP by formulating the routing problem using integer linear programming (ILP). IBM’s ILOG CPLEX was used to obtain an optimal solution to the model. This solution aimed to delay and group messages until as late as possible and then deliver the messages to their destination. However, this solution made the assumption that wireless communication is perfectly reliable, which is not the case. So the optimal solution was recreated by a near-optimal routing algorithm that aimed to produce similar behaviour.
The Impact of Decreasing Transmit Power Levels on FlockLab To Achieve a Sparse Network
When developing techniques for IoT devices, it is preferable to perform testing on real devices in real situations such as on FlockLab 2, FIT IoT-LAB, and INDRIYA 2, as simulation will not perfectly reproduce these environments. However, IoT testbeds are not always deployed in the same scenarios for which techniques are developed for. It is often the case that testbeds are set up in existing facilities (such as inside office buildings) and devices are positioned close to each other. This means that there is currently a lack of testbeds supporting the testing of applications that will be deployed outside, on a large scale, with sparse connectivity. Commonly, the transmission power of device can be reduced in order to emulate a sparse network, this paper looked at the baseline effects of doing so.
PNT Cyber Resilience: a Lab2Live Observer Based Approach, Report 2: Specifications for Cyber Testing Facilities
Global navigation satellite systems (GNSS) such as GPS and Galileo are vital sources of positioning, navigation and timing (PNT) information for vehicles. This information is of critical importance for connected autonomous vehicles (CAVs) due to their dependence on this information for localisation, route planning, and situational awareness. A downside to solely relying on GNSS for PNT is that the signal strength arriving from navigation satellites in space is weak and currently there is no authentication included in the civilian GNSS adopted in the automotive industry. This means that cyber-attacks against the GNSS signal via jamming or spoofing are attractive to adversaries due to the potentially high impact they can achieve. This report introduces specifications and recommendations for GNSS cyber-security test facilities for CAVs. These specifications are based on a survey of academic literature, interviews with a select group of experts, and experiences obtained performing laboratory and real-world testing.
Privacy Challenges with Protecting Live Vehicular Location Context
Previous work on live location privacy protection for vehicle-to-vehicle (V2V) communication has rarely considered multiple sources of identity leakage. This is problematic as vehicles will exhibit multiple sources of identifying information. However, not all of this information will be available to all threat actors. Some identifying information will be easier and cheaper to obtain (e.g., via a sensor network listening for V2V communications) compared to other approaches (e.g., deploying a network of cameras). This paper identified the numerous sources of identity leakage from a vehicle and devices which may be present in it, the threat actors trying to violate the vehicle’s live location privacy, the techniques used to protect privacy, and ways in which identity sources and protection mechanisms can interact.
A Spatial Source Location Privacy-Aware Duty Cycle for Internet of Things Sensor Networks
Source Location Privacy (SLP) is an important problem when monitoring valuable assets with wireless sensors. It is important that sensitive context information, such as the location of an asset, is not revealed to adversaries. These wireless sensors are typically deployed with a limited energy source, so protection approaches need to consider their energy cost. In order to save energy, applications deployed on these devices perform duty cycling, where they aim to spend the majority of their lifetime sleeping. However, arbitrary duty cycling algorithms can lead to delays in messages being sent and received. For SLP algorithms that involve time sensitive messages an arbitrary duty cycle will impact the ability to provide SLP. So this paper proposed a duty cycling algorithm that uses knowledge of the SLP protocol to calculate when to wake up and when to sleep.
Trust Assessment in 32 KiB of RAM: Multi-application Trust-based Task Offloading for Resource-constrained IoT Nodes
There is increasing interest in using highly resource-constrained IoT devices to perform complex tasks. These resources might include limited processing power (e.g., 32MHz CPU), RAM (e.g., 32 KiB to 256 KiB), ROM (512 KiB), and potentially no stable storage. However, because of the limited resources an IoT device may need to offload expensive tasks to resource-rich devices. These might be a Cloud server or an Edge node if the latency of task responses is important. In order to address this issue, in this work we developed a middleware to facilitate task offloading using a measure of behavioural trust.
Trust Trackers for Computation Offloading in Edge-Based IoT Networks
There is increasing interest in using highly resource-constrained IoT devices to perform complex tasks. These resources might include limited processing power (e.g., 32MHz CPU), RAM (e.g., 32 KiB to 256 KiB), ROM (512 KiB), and potentially no stable storage. However, because of the limited resources an IoT device may need to offload expensive tasks to resource-rich devices. These might be a Cloud server or an Edge node if the latency of task responses is important. In most cases, trust is built up reactively where an interaction is performed and the result of that interaction is used to update a trust model. In this work we instead adopt a proactive approach to assessing trust, where a challenge is periodically sent to each resource-rich device that a task could be offloaded to. This challenge is sufficiently expensive for the resource-rich device to compute a result, but cheap for the resource-constrained device to verify.
Attributes and Dimensions of Trust in Secure Systems
In this paper we set out our position on the concept of trust in secure systems. This position evolved from previous work investigating trust-based task offloading. The views in this paper intended to resolve issues that we perceived with the use of trust in literature produced by the security community. To resolve this we provided more general definitions for trust and related concepts, splitting them into the label that is assigned (trusted/trustworthy) and the measurements (trustiness/trustworthiness). We also identified a set of trust attributes that could be applied to this more general definition and explored dimensions along which attributes could be measured.
Information Management for Trust Computation on Resource-constrained IoT Devices
There is increasing interest in using highly resource-constrained IoT devices to perform complex tasks. These resources might include limited processing power (e.g., 32MHz CPU), RAM (e.g., 32 KiB to 256 KiB), ROM (512 KiB), and potentially no stable storage. However, because of the limited resources an IoT device may need to offload expensive tasks to resource-rich devices. These might be a Cloud server or an Edge node if the latency of task responses is important. These Cloud or Edge servers may not always perform tasks correctly or timely. One approach in deciding who to select is to calculate a value of behavioural trust which acts as a predictor for whether the Cloud or Edge will behave well. This could be via a proactive trust assessment, or a reactive trust assessment. However, the same limited resources that necessitate offloading tasks also means that there needs to be a strategy to decide which historical information used to calculate behavioural trust should be kept in memory and which information should be discarded when memory is full.
Quantifying Source Location Privacy Routing Performance via Divergence and Information Loss
There has been much work investigating Source Location Privacy (SLP), including the analysis of techniques. However, one area in which there is a lack of analysis is against adversaries in the network. These adversaries can be cheaply equipped with a laptop, directional antenna and a cheap software defined radio to effectively locate the sources of valuable assets. In this work we investigated how to quantify the amount of information a non-SLP-aware routing matrix reveals to an adversary compared to an SLP-aware routing matrix via a measure of divergence. Using this measure an algorithm was developed to transform a non-SLP-aware routing matrix into an SLP-aware routing matrix.
Threat-Modeling-Guided Trust-Based Task Offloading for Resource-Constrained Internet of Things
There is increasing interest in using highly resource-constrained IoT devices to perform complex tasks. These resources might include limited processing power (e.g., 32MHz CPU), RAM (e.g., 32 KiB to 256 KiB), ROM (512 KiB), and potentially no stable storage. However, because of the limited resources an IoT device may need to offload expensive tasks to resource-rich devices. These might be a Cloud server or an Edge node if the latency of task responses is important. In order to address this issue, in this work we developed a middleware to facilitate task offloading using a measure of behavioural trust. In addition, we also performed a threat modelling on the system to identify ways in which malicious Edge nodes could attempt to manipulate reputation in order to hide their bad actions and ways in which this could be mitigated.
NewSpace, New Threats -- Exploring the Influence of New Entrants to the Space Industry on Cybersecurity
The space sector is seeing rapid growth amongst commercial organisations, giving rise to NewSpace. Established organisations involved in the space sector or typically governmental or private sector organisations for which there has been a need to secure the system’s deployed. However, new small to medium sized enterprises (SMEs) entering the sector encounter challenges ensuring the security of their system. In this paper we undertook 8 semi-structured interviews to explore perspectives on space cyber security.
SlowCoach: Mutating Code to Simulate Performance Bugs
It is important that software runs fast. Better performance means that software is more responsive, consumes less energy, and provides less scope for adversaries to perform denial of service attacks that take advantage of poor performance. In order to identify performance issues, diagnosis tools need to be used to analyse software performance. Like other software, it is important that we are able to investigate the efficacy of performance diagnostic tools (such as perf). Mutation testing has been used to analyse the performance of a test suite’s ability to detect bugs in code. This is done by injecting mutations which leads to incorrect behaviour in the source code, and allows evaluation of the test suite’s capability to detect that inserted mutation. In this paper we extend the idea of mutation testing to performance mutation testing, in order to be able to test how well performance diagnostic tools are able to detect performance bugs.
Towards Effective Performance Fuzzing
Fuzzing is a process that generates a large number of inputs to provide to a program with the intent to identify bugs. These inputs are generated by a fuzzer following some set of rules. Fuzzers typically focus on correctness bugs, however, also of importance are bugs that lead to poor performance. For example, bugs that cause a large number of hash collision can significantly reduce the performance of hash tables from amortized O(1) to O(n). This is a security vulnerability as the reduced performance can lead to loss of availability in applications. Examples of this type of vulnerability has occurred in the implementation of Python.
Security-Minded Verification of Cooperative Awareness Messages
The process of identifying threats to systems via threat modelling is often kept separate from the process of formally proving correctness of systems. In this paper we present a hybrid approach to performing both methodologies simultaneously via an example case-study of Cooperative Awareness Messages used by Connected Vehicles. By using this hybrid approach security properties can be identified and formally verified.
Poster: Effectiveness of Moving Target Defense Techniques to Disrupt Attacks in the Cloud
Cloud systems are now highly pervasive and provide significant opportunities for adversaries to attack these systems. One approach to mitigate the amount of time adversaries have to attack a system is to reconfigure the system, in essence to provide a moving target that adversaries need to contend with. The advantage of moving target defence (MTD) that adversaries have less time to perform reconnaissance and then attack a system. The moving target could be to change IP addresses — so adversaries are unsure of network structure, or to change the operating system and applications providing a service — so adversaries may struggle to exploit a vulnerability in specific software. Cloud systems are simultaneously well suited to MTD due to their ability to be dynamically reconfigured and challenging to apply MTD due to the wide variety of ways in which it can be employed. This means there is a need to be able to effectively select where MTDs should be applied in a cloud environment.
Poster: Multi-Layer Threat Analysis of the Cloud
Cloud systems are now highly pervasive and provide significant opportunities for adversaries to attack these systems. Therefore, there is a need to understand how attacks can be performed in a Cloud environment. It is important to perform this analysis for historical attacks — to analyse what happened and what alternate routes an adversary could have taken to reach their goals. However, it is also important to have a capability to perform speculative analysis in terms of what potential attacks could have been performed considering a specific set of vulnerabilities. Therefore, this work investigated modelling the dynamic cloud environment, threats to it and how an adversary could reach specific goals.
Enabling Multi-Layer Threat Analysis in Dynamic Cloud Environments
Cloud systems are now highly pervasive and provide significant opportunities for adversaries to attack these systems. Therefore, there is a need to understand how attacks can be performed in a Cloud environment. It is important to perform this analysis for historical attacks — to analyse what happened and what alternate routes an adversary could have taken to reach their goals. However, it is also important to have a capability to perform speculative analysis in terms of what potential attacks could have been performed considering a specific set of vulnerabilities. Therefore, this work investigated modelling the dynamic cloud environment, threats to it and how an adversary could reach specific goals.
Security-by-design Securing a compromised system
There has been a large effort to sell a concept of secure-by-design by both the UK, USA and others. The reality is that being secure-by-design is not realistic.
Talks
Warwick Postgraduate Colloquium in Computer Science
The Warwick Postgraduate Colloquium in Computer Science (WPCCS) is a PhD student-run event which showcases the research performed by PhD students in the Department of Computer Science at the University of Warwick. I was chair of WPCCS 2016 and a member of the programme committee for WPCCS 2017 and WPCCS 2018. Each year we received more presentations and posters submitted to the event as we tried to increase the event’s similarity to conferences PhD students would attend.
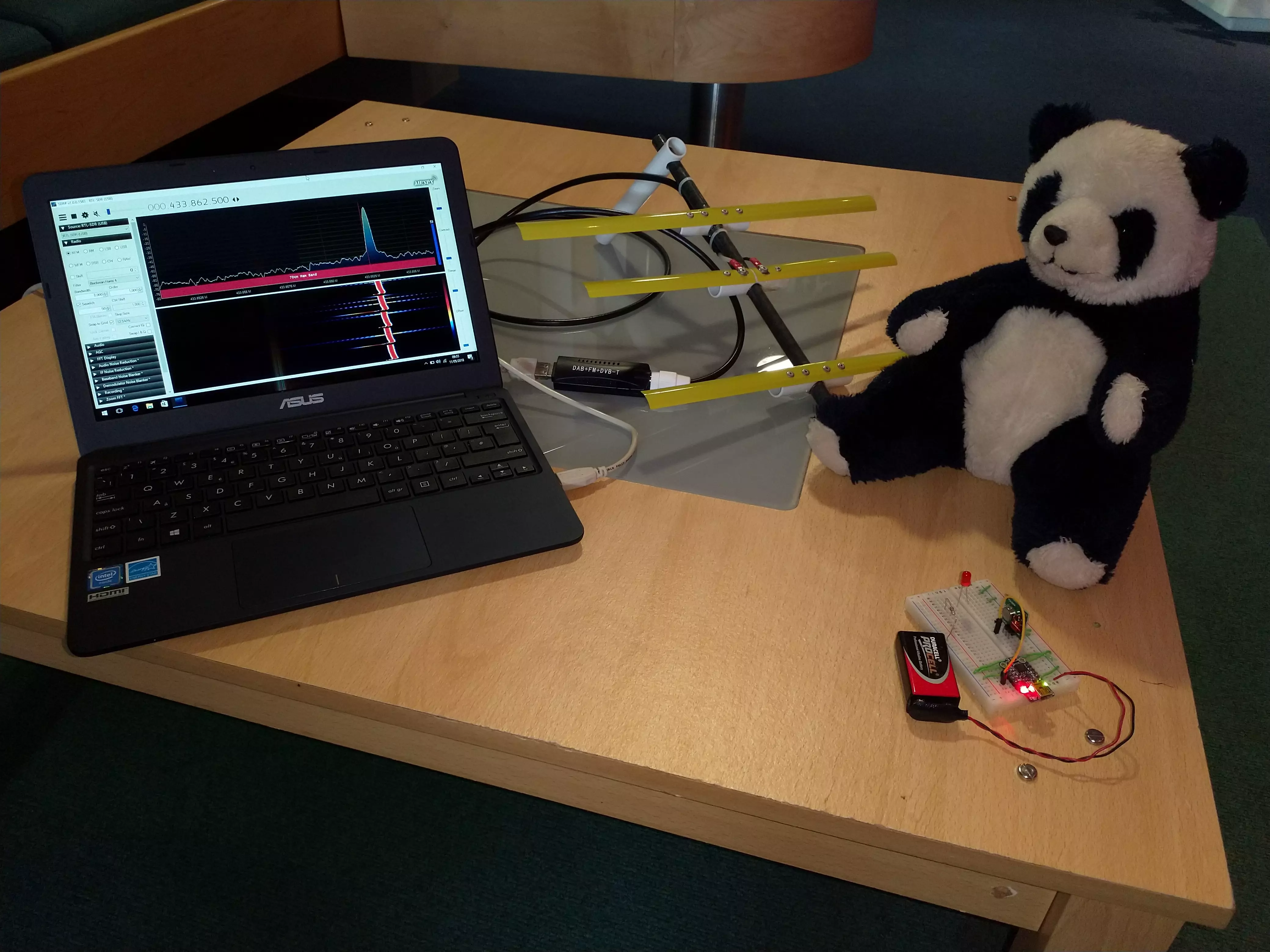
How To Stop Poachers Stealing Your Pandas
Pint of Science is an annual event where researchers share their work in a informal context (the pub) with the general public. The aim of these events is to inform in a relaxed environment without the pressures of a formal academic setting. This talk covered research undertaken during my PhD and included a live demonstration of members of the public using a directional antenna to find the location of a small transmitter.
Space Security Scoping Workshop
As part of the FAIR-SPACE project a workshop was held with members of academia and industry to identify cyber-security issue with robotic systems deployed in space and to scope out which of these issues were of high priority. Dr. Marie Farell and myself led the discussion with the attendees after introductory talks from Prof. Michael Fisher and Prof. Carsten Maple.
Competitive Advantage in the Digital Economy (CADE) Forum
The Competitive Advantage in the Digital Economy (CADE) Forum aims to bring together academics and practitioners to discuss the challenges of the digital economy and present the latest cutting edge research. I was the Program Chair for the 2019 forum and that year the event focused on Smart Service Systems, Personal Data and Cyber Security. There were 28 speakers and 5 keynote speakers who gave presentations on a wide variety of topics. Funding to hold the event was obtained from a variety of sources, including winning funding from Warwick’s Institute of Advanced Study.
Orbit RRI Ethical Hackathon on Cyber Security
ORBIT’s aim is to promote Responsible Research and Innovation (RRI) to ensure the sustainability, acceptability and desirability of research. As part of this goal in June of 2019 they ran an Ethical Hackathon on Cyber Security of satellite systems. I was invited to give a guest talk on work applying formal verification to prove security properties of space systems being performed in the FAIR-SPACE hub. The summary of the event highlighted the depth understanding participants gained of RRI issues related to cyber security.
Towards Security Minded Verification: A Case Study of Cooperative Awareness Messages
I was invited to give a talk to Coventry University’s Institute for Future Transport and Cities on my work performed for FAIR-SPACE which investigated a formal verification of security properties of the generation of Cooperative Awareness Messages. One of the conclusions of this presentation was the difficulty of verifying non-functional security properties.
Trust Assessment in 32 KiB of RAM: Multi-application Trust-based Task Offloading for Resource-constrained IoT Nodes
There is an increasing demand for Internet of Things (IoT) systems comprised of resource-constrained sensor and actuator nodes executing increasingly complex applications, possibly simultaneously. IoT devices will not be able to execute computationally expensive tasks and will require more powerful computing nodes, called edge nodes, for such execution, in a process called computation offloading. When multiple powerful nodes are available, a selection problem arises: which edge node should a task be submitted to? This problem is even more acute when the system is subjected to attacks, such as DoS, or network perturbations such as system overload. In this presentation,a trust model-based system architecture for computation offloading is presented. The system architecture provides confidentiality, authentication and non-repudiation of messages in required scenarios and will operate within the resource constraints of embedded IoT nodes. The viability of the architecture is demonstrated with an example deployment of Beta Reputation System trust model on real hardware.
Trust Trackers for Computation Offloading in Edge Based IoT Networks
Wireless Internet of Things (IoT) devices will be deployed to enable applications such as sensing and actuation. These devices are typically resource-constrained and are unable to perform resource-intensive computations. Therefore, these jobs need to be offloaded to resource-rich nodes at the edge of the IoT network for execution. However, the timeliness and correctness of edge nodes may not be trusted (such as during high network load or attack). In this presentation, we look at the applicability of trust for successful offloading. Traditionally, trust is computed at the application level, with suitable mechanisms to adjust for factors such as recency. However, these do not work well in IoT networks due to resource constraints. We propose a novel device called Trust Tracker (denoted by Σ) that provides higher-level applications with up-to-date trust information of the resource-rich nodes. We prove impossibility results regarding computation offloading and show that Σ is necessary and sufficient for correct offloading. We show that, Σ cannot be implemented even in a synchronous network and we compute the probability of offloading to a bad node, which we show to be negligible when a majority of nodes are correct. We perform a small-scale deployment to demonstrate our approach.
Next Generation Programmers
Next Generation Programmers was an event aimed to introduce programming to young adults (14 – 17 years old) in rural Kazakhstan which was organised by Dr. Torgyn Erland. I delivered three 1 hour sessions to introduce the attendees to software development, the interesting problems that can be solved using it, and pertinent cyber security issues that the attendees were likely to encounter.
Wildlife Conservation: Can AI Make Poachers the Poached?
As part of my PhD I investigated approaches to reduce the usefulness of contextual information gained by an adversary monitoring a network that itself is used to monitor wildlife. In this podcast hosted by PETRAS’ Joe Bourne, Grant Miller from ZSL and I discuss a variety of topics around wildlife protection. This included the need to consider context privacy threats in these systems and also additional uses and challenges with techniques such as machine learning.
Automating Threat Modelling
The Lancashire Cyber Crime Conference was hosted by the Lancashire Constabulary and the Lancashire Cyber Foundry to assist businesses in staying safe. The Lancashire Cyber Foundry aims to support small to medium enterprises (SMEs) in the Lancashire area using digital technologies. This includes raising awareness and supporting SMEs with cyber security. In the first half of this talk I introduce SMEs to academia and the ways in which SMEs can engage and collaborate with academic researchers. In the second half of this talk I introduce threat modelling, and briefly discuss some of my past work and how some future work is allowing for greater automation of threat modelling.
Generalised Context Privacy
The Academic Centres of Excellence in Cyber Security Research aim to recognise the universities in the UK which are conducting world leading cyber security research. At this event members of ACE-CSRs attended and presented current and future work. In this presentation I set out the case for addressing Context Privacy in general in order to deliver the ability to rapidly respond to new Context Privacy Threats.
Lancaster Symposium on Systems Security 2022
The Lancaster Symposium on Systems Security (LS3) is a PhD student-led event (supervised by myself) which aims to bring together researchers from within Lancaster University’s System Security Group to share and explore the latest research on the security and privacy of computer systems and networks. The theme for 2022 was “Novel Challenges in System Security”, focusing on new research within the area of system security.
Threat Modelling Guided Trust-based Task Offloading for Resource-constrained Internet of Things
Resource-constrained IoT devices have traditionally been used for basic tasks such as sensing or actuating, but there is increasingly more interest in pushing complex applications closer to where digital systems interact with their environment. This presentation of a journal paper summarised work on trust-based task offloading and potential security issues wheile doing so.
Safe as houses
In this podcast I talk about a wide variety of cyber physical systems and possible threats. This includes drones and resource-constrained IoT boards that are being assembled for the Generalised Context Privacy project. In this project the core problem that is being looked at is the amount of information that cyber physical systems convey to an adversary. This podcast highlights the difference between data versus information, especially the information that an adversary gains from observations. A real challenge remains that cyber security fundamentals remain hard for organisations, so challenging threats such as these are rarely considered.
Generalised Context Privacy
The Lancashire Cyber Festival 2023 brought together academic researchers, industry and defence in the Lancashire region to continue to build upon the concentration of cyber skills, experience and leadership in the region. The event was also used to launch the Lancashire Cyber Partnership of which Lancaster University is a partner.
Generalised Context Privacy
There has been significant effort on addressing data content threats, whether this be to data in motion, data at rest or a private release of data. However, for systems being directly observed by an adversary, risks exist in the form of information revealed by the actions a system takes and the context in which it takes them. Thus, considering the context privacy of a system is important from a holistic viewpoint. Context privacy techniques already exist in a wide range of different domains (e.g., onion routing, location privacy in ad-hoc networks), but we lack the ability to rapidly develop novel techniques when new context privacy threats are identified. To address this, privacy quantification approaches and techniques will be developed for an arbitrary system, which will subsequently be used in translators for specific systems of interest. This presentation sets out the problem and explores initial work on quantification being performed in a recently funded EPSRC project.
Teaching Penetration Testing
At a Lancaster University education event, I presented work that I have been undertaking to improve the delivery of SCC.442 Penetration Testing. There were three main problems that had been encountered in previous years:
- Students had unclear expectations in terms of what was expected from them
- Students struggled to approach technical problems in assessments
- Manual construction of lab and assessment material was time-consuming and unreliable